The Small
Business
Cyber Security Guy
⭐100K+ Monthly Downloads | ⭐Top 20 Apple Management | 🎧>2.5K per episode
Welcome to the blog and podcast, where we share brutally honest views, sharp opinions, and lived experience from four decades in the technology trenches. Whether you're here to read or tune in, expect no corporate fluff and no pulled punches.
Everything here is personal. These are my and the team’s thoughts, not those of our employers, clients, or any poor soul professionally tied to me. If you’re offended, take it up with me, not them.
What you’ll get here (and on the podcast):
Straight-talking advice for small businesses that want to stay secure
Honest takes on cybersecurity trends, IT malpractice, and vendor nonsense
The occasional rant — and yes, the occasional expletive
War stories from the frontlines (names changed to protect the spectacularly guilty)
I've been doing this for over 40 years. I’ve seen genius, idiocy, and everything in between. Some of it makes headlines, and most of it should.
This blog and the podcast is where we unpack it all. Pull up a chair.
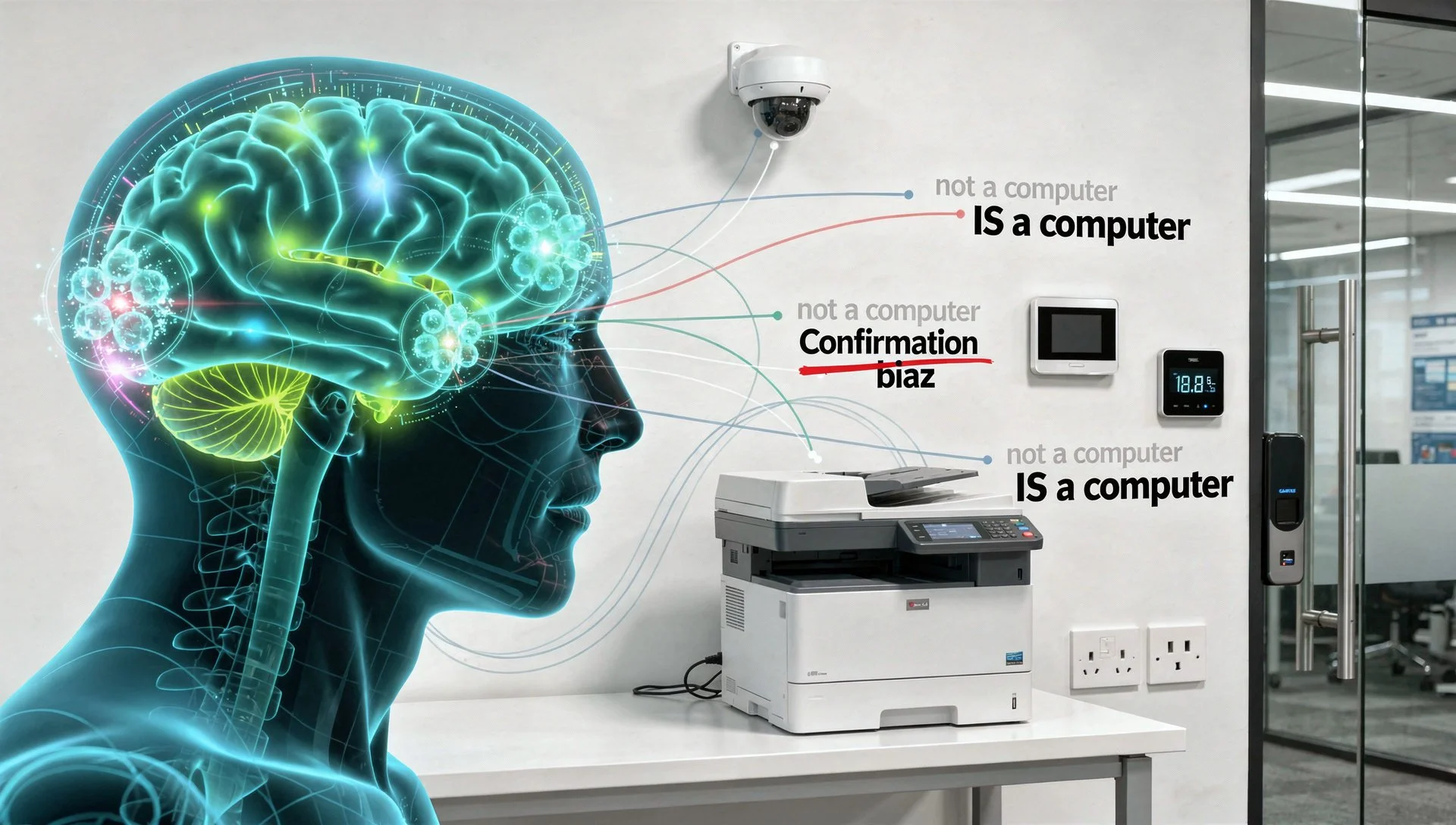
Why Smart People Keep Ignoring Smart Device Security: The Psychology Behind IoT Blindness
After this week's podcast revelation about the marketing agency losing client files through an unsecured printer, my inbox has been full of variations on the same question: how do intelligent business owners with otherwise solid security miss something this obvious?
The answer isn't comfortable, but it's important: IoT security failures aren't about lack of intelligence. They're about systematic psychological blind spots that affect everyone from small business owners to government departments.
Former UK Government analyst reveals the cognitive biases costing UK businesses millions and, more importantly, how to overcome them before your next security decision. Understanding the psychology prevents the breach.
Your £15,000 Security Investment Just Got Defeated by a £300 Printer
Right, let's talk about the £15,000 security investment that just got absolutely destroyed by a £300 office printer. A marketing agency did everything right: new firewalls, endpoint protection, hardware authentication keys for every staff member, security audit came back clean. Two months later? Someone had been accessing their client files for weeks through their HP printer still using admin/admin as credentials. While you've been securing laptops and servers, your printer has full network access, stores every document you print, and still uses the password it shipped with. Pull up a chair, this intervention is long overdue.
The Devices You Forgot Were Computers - IoT Security for Small Business
What if I told you the biggest cyber threat to your business isn't hackers, but your office printer? Sounds mad, right? That's what a 30-person marketing agency thought before someone accessed their client files for weeks through an HP printer with factory default credentials. Episode 30 reveals the devices everyone forgets are computers: printers storing documents, CCTV systems livestreaming your premises, thermostats providing network access. Currently Top 12 in Apple Podcasts Management category worldwide with 3,500 daily downloads. Thirty episodes making cybersecurity almost entertaining whilst being brutally honest. Listen now. Check your printer later. You'll understand why.
The Complete SMB Toolkit for Reverse Benchmarking: Free and Budget Tools That Actually Work
Right, enough theory. Today we're getting practical: the actual tools, templates, and processes you need to implement reverse benchmarking without spending a fortune. Everything in this guide is either free or costs less than a decent takeaway curry per month. Because I'm sick of "enterprise security" guides that assume unlimited budgets and dedicated staff. This is the real-world, shoestring-budget, one-person-wearing-multiple-hats implementation guide. Asset inventory using Google Sheets: free. Vulnerability scanning with OpenVAS: free. MFA with authenticator apps: free. Security advisories via email: free. The British Library spent £7 million recovering from ransomware. Prevention would have cost £10,000-20,000 annually. Budget isn't your excuse anymore.
The Psychology of Security Failures: Why Smart People Keep Making the Same Stupid Mistakes
Noel spent Monday and Tuesday explaining what reverse benchmarking is and how to implement it technically. Both excellent.
Both necessary. Both completely inadequate if you don't understand why organizations systematically fail to learn from disasters. Here's the uncomfortable truth: most breaches happen not because organisations don't know what to do, but because human psychology actively prevents them from doing it.
Normalcy bias makes us believe disasters happen to others. Optimism bias creates illusions of control. Blame cultures suppress incident reporting. The fundamental attribution error prevents learning from failures. Your brain evolved for different threats in different environments. The cognitive biases that kept us alive now get us breached.
When Security Royalty Gets It Dangerously Wrong: Debunking the "Stop Hacklore" Letter
86 security professionals including former CISA director published advice last year claiming public WiFi, QR codes, and USB charging stations are safe.
Sounds credible, except I've spent the year mopping up after businesses who followed exactly this advice. £47,000 stolen via hotel WiFi. Companies breached via QR code phishing. Legal practice ransomwared through compromised charging station.
When security elite operate in enterprise bubbles with unlimited budgets, their advice becomes dangerous for SMBs without those luxuries.
Here's the evidence-based reality, complete with actual incident costs and why defence in depth isn't folklore.
Reverse Benchmarking: Why Studying Cyber Failures Beats Copying Best Practices
Most people copy what the big players do and call it a cyber strategy. That works for them. It probably kills you. This episode flips the script. Instead of worshipping best practice, we dissect the car crashes.
Target, Equifax, Colonial Pipeline and SolarWinds. We ask one question. What actually went wrong and have you quietly made the same mistakes in your own business.
If you run a UK small or mid sized firm and feel lost in security buzzwords, this is your shortcut. Learn from other peoples disasters before you become the next case study. Your future self will approve.
The Comfortable Lie: Why UK Cybersecurity's Status Quo Is No Longer Defensible
Let's drop the diplomatic language for a moment. Current UK cybersecurity regulation is a comfortable lie we tell ourselves to avoid uncomfortable truths. We pretend fines deter when they don't. We pretend guidance works when it doesn't. We pretend breaches are inevitable when most are preventable.
Meanwhile, millions of citizens have their data compromised by organisations that face no meaningful consequences. The Synnovis attack contributed to patient deaths. The ICO's response? Under investigation. Still.
The comfortable lie protects negligent directors whilst citizens pay the price. It's time to stop pretending.
When Enforcement Gets Teeth: UK Case Studies in Accountability That Works
Numbers don't lie. In 1981, 495 workers died in British workplaces. The most recent figures show 124. That's not technological progress alone. That's regulatory teeth. When the Health and Safety Executive gained proper enforcement powers, directors discovered that ignoring safety had personal consequences. Prosecutions made headlines. Behaviour changed. Industries transformed. Today, we examine exactly how HSE enforcement worked and exactly what similar cybersecurity enforcement could achieve. These aren't hypothetical projections. They're evidence-based extrapolations from 50 years of proven regulatory success.
Demonstrating Reasonable Care: Your Practical Guide to Cybersecurity Accountability
Enough theory. Today we're getting practical. Whether or not director liability becomes law, demonstrating reasonable care protects your business now. Insurance claims require evidence. Contracts demand due diligence.
Regulators ask what you did before the breach. This guide gives you exactly what you need: the five controls that matter, documentation templates, evidence gathering processes, and realistic timelines for businesses of every size.
No enterprise consultants required. No massive budgets necessary. Just clear steps to prove you took security seriously before anyone asks you to prove it.
Why Personal Accountability Changes Everything: The Psychology of Director Liability
After two days discussing frameworks and technical standards, let's examine why personal accountability actually works when corporate fines consistently fail. The psychology is fascinating and explains decades of regulatory success and failure.
When British Airways faced a £20 million fine, nobody lost their job. When HSE prosecutes directors, workplace safety transforms overnight. The difference isn't the amount of money. It's whose money gets spent and whose freedom gets threatened. Human psychology responds very differently to personal consequences versus corporate abstractions.
The Three-Tier Cybersecurity Liability Framework: What It Means for Your Business
Yesterday's podcast proposed criminal liability for cybersecurity negligence. Today, we're dismantling the three-tier framework piece by piece so you know exactly where your business stands. Tier One protects small businesses with explicit gross negligence thresholds and Cyber Essentials safe harbour. Tier Two raises the bar for medium organisations whilst maintaining proportionate standards. Tier Three brings genuine consequences for large enterprises and public sector bodies that still can't implement MFA. This isn't fear-mongering. It's showing you precisely what reasonable care looks like at every business size so you can demonstrate compliance before anyone asks.
Prison Time for Directors? Part 2: Building the UK Cybersecurity Accountability Framework
Yes, you read that correctly. Prison time for directors who allow catastrophic cybersecurity failures. Before you close this tab in horror, hear me out. We already send directors to prison for health and safety failures. Workplace fatalities dropped 85% after the Health and Safety Executive got proper enforcement powers. The ICO? They send sternly worded letters whilst breaches affecting millions go unpunished. Today, Mauven and I lay out exactly what a proper UK cybersecurity enforcement regime would look like - one that protects small businesses whilst holding negligent executives accountable. Pull up a chair.
Designing the Corporate Cyber Negligence Act (What Accountability Looks Like)
This week, we established why directors should face criminal prosecution for gross cybersecurity negligence. We examined the Synnovis case where a patient died because free MFA was not enabled. We provided technical analysis, psychological examination, and practical implementation guides. Saturday's opinion piece argued forcefully for criminal liability. Next week, we move from "why" to "how."
What would a Corporate Cyber Negligence Act actually say? What are the thresholds between bad luck and criminal negligence? How do we protect small businesses while targeting genuine negligence? What defences exist? How would enforcement work? We are designing the solution. Join us Monday.
Enough. It Is Time to Send Negligent Directors to Prison for Cyber Failures.
I am tired of watching preventable disasters kill people while executives walk away with bonuses intact.
A patient died because Synnovis did not enable free multi-factor authentication. Nobody will face criminal prosecution.
If a construction director failed to provide hard hats and a worker died, that director would go to prison.
Yet when healthcare executives fail to enable free security controls and a patient dies, nothing happens. This is not justice. This is not accountability.
This is a broken system that treats cybersecurity negligence as an acceptable cost of doing business. It needs to stop. Here is why directors should face prison time for gross cyber negligence.
The Synnovis Ransomware Disaster: Complete Timeline and Technical Analysis
On 3 June 2024, the Qilin ransomware gang compromised Synnovis, a pathology provider serving NHS hospitals across southeast London. Blood testing collapsed. Over 10,000 appointments were cancelled. More than 1,700 operations were postponed. A patient died waiting for test results that never arrived. The attack succeeded because multi-factor authentication was not enabled. Here is the complete timeline of how a preventable security failure cascaded into catastrophic harm, the technical details of the attack vector, the devastating human and financial cost, and what every UK business must learn from this disaster. This is what happens when free security controls are ignored.
How to Implement MFA Across Your Business in One Afternoon (Complete Guide)
After this week's coverage of the Synnovis death, many of you have asked: "How do I actually implement MFA in my business?" Here is your complete, practical guide. No jargon, no theory, just step-by-step instructions for enabling multi-factor authentication across your entire organisation. This afternoon. Right now. Whether you are running Microsoft 365, Google Workspace, or a mix of different services, this guide walks you through the exact process. I will show you how to configure systems, deploy authenticator apps, train your staff, and create backup plans for when people lose their phones. Let’s prevent another preventable disaster from happening to your business.
The Psychology of Cybersecurity Negligence: Why Smart People Make Fatal Decisions
Nobody wakes up and decides to let patients die through cybersecurity negligence. Yet that is precisely what happened at Synnovis. The executives who failed to enable multi-factor authentication were not cartoon villains.
They were educated professionals running a critical healthcare organisation. So why did they make a decision that, in hindsight, seems obviously catastrophic?
The answer lies in the psychological mechanisms that allow intelligent people to rationalise terrible choices, the organisational structures that insulate decision-makers from consequences, and the systemic failure to connect cybersecurity decisions to real-world harm.
Understanding this psychology is essential to preventing the next preventable death.
Why Multi-Factor Authentication Could Have Prevented the Synnovis Death
When Beverley Bryant, former Chief Digital Information Officer at Guy's and St Thomas' NHS Foundation Trust, stated that the Synnovis attack "may not have happened" with two-factor authentication enabled, she was not speculating. She was describing technical reality.
The Qilin ransomware gang gained initial access through compromised credentials. Multi-factor authentication completely blocks this attack vector.
A patient died because a free security control was not enabled. This is not hindsight; it is basic cybersecurity hygiene that has been industry standard for over a decade.
Here is the technical explanation of exactly how MFA would have stopped this attack.
Should Directors Face Prison Time for Cybersecurity Negligence?
On 3 June 2024, a patient arrived at a London hospital A&E feeling unwell. A blood test was ordered. The patient waited. The medics waited. They all waited some more. The patient died. Why? Ransomware had shut down blood testing at Synnovis, the NHS pathology provider.
The security control that would have stopped it? Multi-factor authentication. Completely free. Built into every platform. The consequences for executives who chose not to enable it?
Nothing. In this episode, we ask the uncomfortable question: what if directors faced prison time for gross cybersecurity negligence, just like they do for health and safety failures?
⚠️ Full Disclaimer
This is my personal blog. The views, opinions, and content shared here are mine and mine alone. They do not reflect or represent the views, beliefs, or policies of:
My employer
Any current or past clients, suppliers, or partners
Any other organisation I’m affiliated with in any capacity
Nothing here should be taken as formal advice — legal, technical, financial, or otherwise. If you’re making decisions for your business, always seek professional advice tailored to your situation.
Where I mention products, services, or companies, that’s based purely on my own experience and opinions — I’m not being paid to promote anything. If that ever changes, I’ll make it clear.
In short: This is my personal space to share my personal views. No one else is responsible for what’s written here — so if you have a problem with something, take it up with me, not my employer.