When Your Firewall Vendor Starts Dropping Weekly CVEs
A UK SMB Guide to Staying Safe and Knowing When to Move On
Why This Matters Right Now
Your firewall is not just a piece of hardware sitting in a rack. It is a complex software platform, and like any software, it has bugs. The difference is that bugs in your perimeter security appliance can give attackers direct access to your entire network. When those bugs start appearing weekly and attackers are already exploiting them in the wild, "security update" stops being a routine task and becomes an urgent business continuity issue.
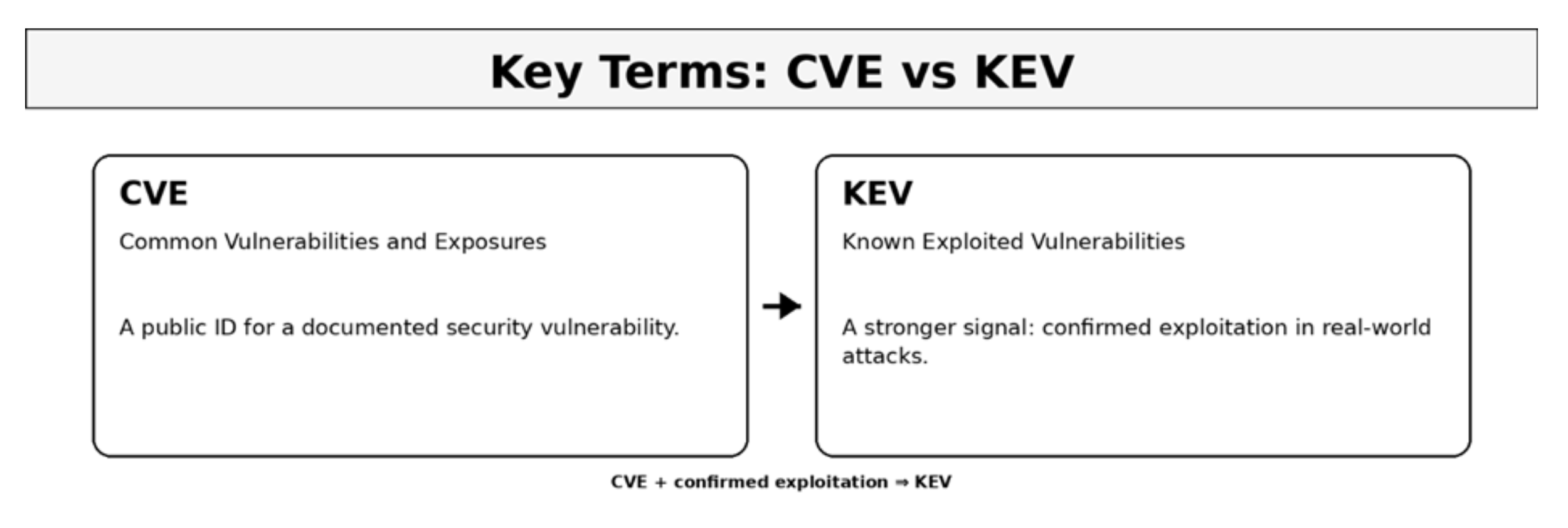
For UK SMBs relying on popular firewall vendors like Fortinet and SonicWall, the past year has brought an uncomfortable reality: both vendors have had multiple vulnerabilities added to CISA's Known Exploited Vulnerabilities catalogue. This is not speculation or security vendor marketing. This is documented, confirmed exploitation in real attacks against real organizations.
Figure 1: Understanding CVE and KEV designations
What Changed This Week
Fortinet: Fresh KEV Addition Under Active Exploitation
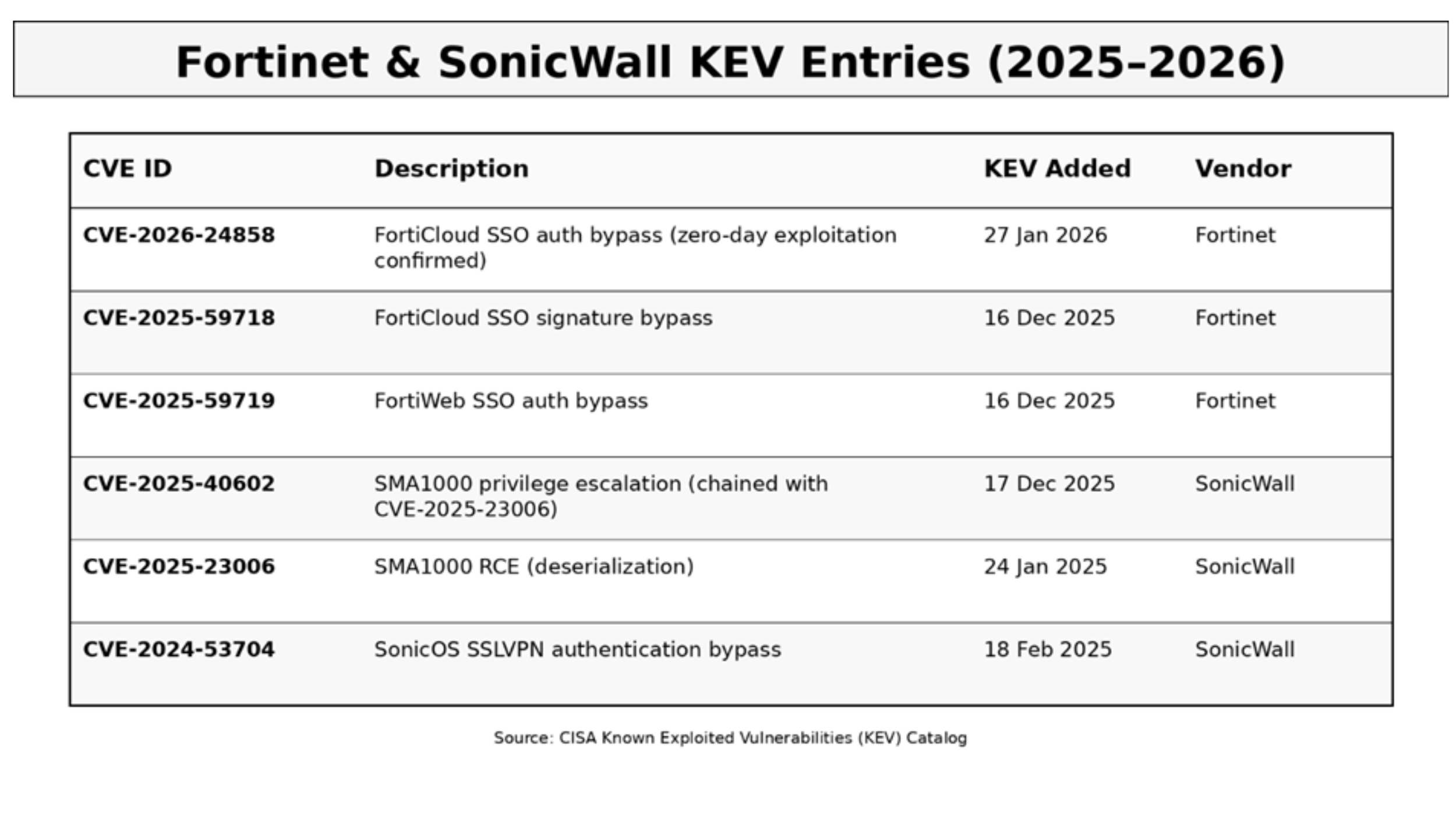
On 27 January 2026, CISA added CVE-2026-24858 to the Known Exploited Vulnerabilities catalogue. This critical vulnerability affects FortiOS, FortiManager, FortiAnalyzer, and FortiProxy. The flaw allows an attacker with a FortiCloud account and a registered device to log into other devices registered to completely different accounts, provided FortiCloud SSO authentication is enabled.
In plain terms: if your organization uses FortiCloud single sign-on (which gets enabled automatically when you register devices through the GUI unless you explicitly disable it), an attacker could potentially access your firewall through the cloud authentication system. Fortinet confirmed this vulnerability was being exploited as a zero-day before disclosure, with two malicious FortiCloud accounts identified and blocked on 22 January 2026.
For SMBs, the practical implication is clear: KEV additions collapse your patch window from weeks to days. When a vulnerability is known to be actively exploited, waiting for your normal monthly maintenance window is no longer acceptable. You need emergency procedures.
SonicWall: No New KEV This Week, But Recent History Demands Attention
SonicWall has not had a new KEV addition in the past few days, but that should not create a false sense of security. In December 2025, CVE-2025-40602 was added to the KEV catalogue after researchers discovered it being chained with CVE-2025-23006 to achieve unauthenticated remote code execution on SMA1000 appliances. Earlier in 2025, CVE-2024-53704, an SSLVPN authentication bypass, was also added to KEV.
The absence of news this week does not mean the absence of risk. Remote access appliances remain high-value targets, and any organization running SonicWall VPN solutions should be conducting a thorough vendor risk conversation.
The Evidence: 2025-2026 Exploitation Patterns
The following table summarizes KEV-listed vulnerabilities for Fortinet and SonicWall products from 2025 into early 2026. This data comes directly from the CISA Known Exploited Vulnerabilities catalogue, the authoritative source for confirmed exploitation.
Figure 2: Recent KEV entries for Fortinet and SonicWall products
The pattern here is not "vendor bad" in some absolute sense. Both Fortinet and SonicWall make products used by thousands of organizations worldwide. The pattern is that vendor risk has operational consequences, and SMBs need a repeatable, systematic response rather than reacting to each disclosure in isolation.
Authentication bypass vulnerabilities are particularly dangerous because they often affect internet-facing management interfaces or VPN services. An attacker does not need to be inside your network first. They can reach these services directly from the internet, and if the vulnerability allows authentication bypass, they can gain administrative access without valid credentials.
What a CVE Wave Does to UK SMBs
Direct costs accumulate quickly when your firewall vendor starts dropping weekly fixes. Emergency patching pulls your IT team or MSP away from planned work. Unplanned maintenance windows create downtime risk. If exploitation does occur, incident response and forensic investigation costs can run into tens of thousands of pounds, not counting regulatory notification requirements or legal exposure.
Indirect costs are harder to quantify but equally real. Cyber insurance providers are increasingly asking detailed questions about patch management practices and perimeter security. A string of emergency patches may trigger premium increases or coverage restrictions at renewal. Customer confidence erodes when your security posture appears reactive rather than controlled. Internal productivity suffers when staff cannot trust remote access or when systems are repeatedly taken offline for urgent updates.
UK context: This is precisely why UK baseline security schemes emphasize both patching discipline and secure configuration. The NCSC's Cyber Essentials scheme, recently reinforced by the Supply Chain Playbook, treats timely patching and secure configuration as foundational controls. When your perimeter vendor makes these controls difficult to maintain, the business case for change becomes clearer.
Action Plan Part 1: Triage Playbook
This checklist is designed for business owners to hand to their IT lead or MSP. It provides a systematic response when your firewall vendor announces a new vulnerability.
Same Day: Inventory and Exposure Check
First, confirm which devices you have and how they are exposed. Which appliances are internet-facing? What services are accessible from outside your network? This typically includes VPN portals, management interfaces (especially web-based GUI access), and cloud login features like FortiCloud SSO. Document running firmware versions and check whether automatic updates are enabled. If you cannot answer these questions within hours, your asset inventory needs immediate attention.
24-72 Hours: Patch Decision Rules
If the vulnerability is KEV-listed, treat it as urgent. Your patch window is days, not weeks. If patching is operationally risky (critical systems depend on the appliance, change windows are restricted), create a short emergency maintenance window rather than delaying. Have a rollback plan ready. Snapshot configurations before applying updates. Test basic connectivity immediately after patching.
Compromise-Aware Steps
Because KEV listings imply that exploitation is already happening somewhere, assume that attackers may have already attempted to compromise your devices. Rotate administrative credentials where appropriate. Review authentication logs for unfamiliar IP addresses, unexpected login times, or new account creation. Check device configurations for unauthorized changes. Restrict management access to internal networks only, use IP allowlists, or require jump box access for administration.
Action Plan Part 2: The Vendor Decision Framework
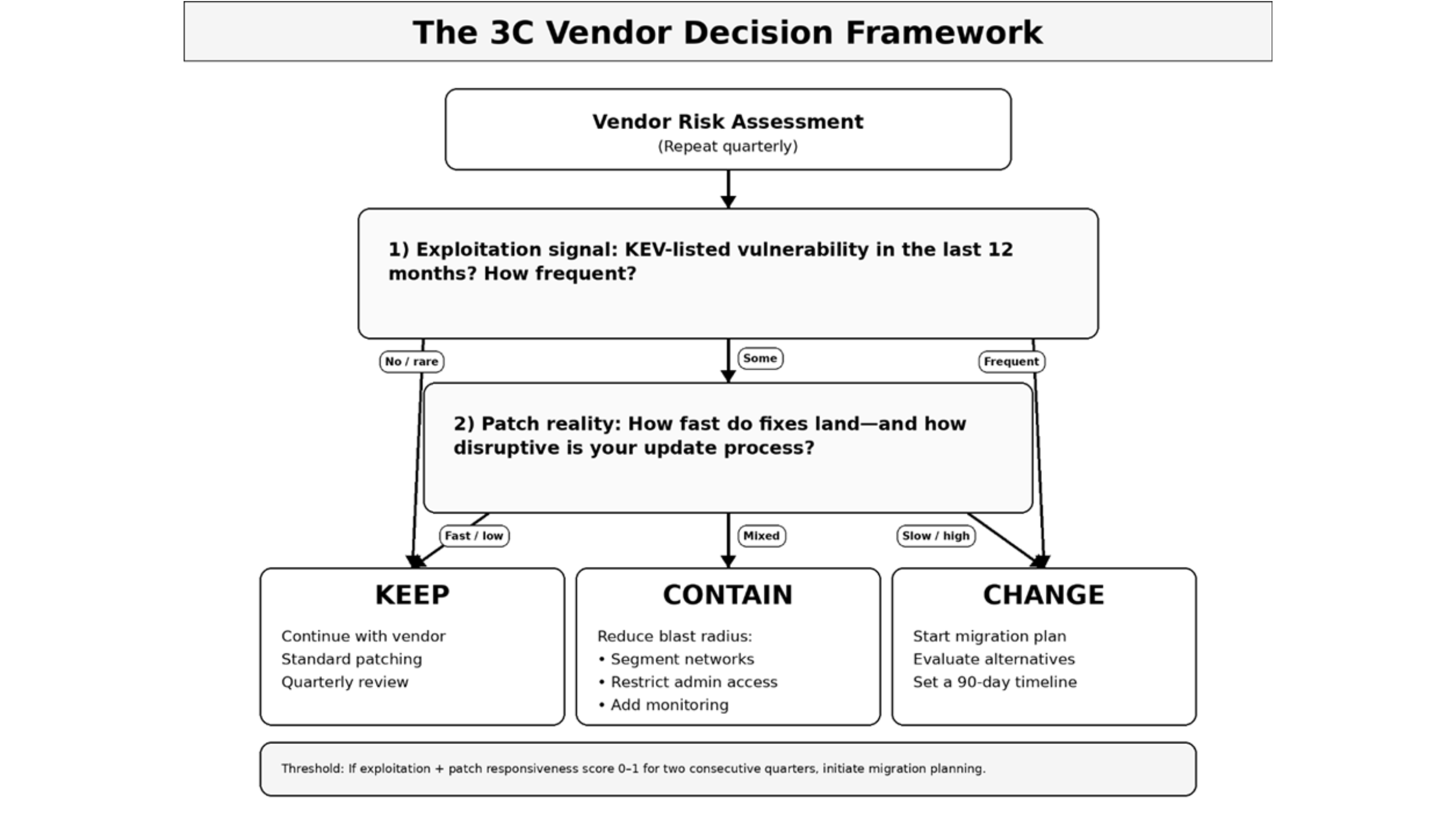
When vulnerability disclosures become routine, you need a structured way to decide whether to stay with your current vendor or begin planning a transition. The 3C model provides a framework: Contain, Compensate, or Change.
Figure 3: The 3C vendor decision framework
Keep means continuing with your current vendor under normal operations. This is appropriate when the vendor's track record shows rare KEV listings, responsive patching, minimal operational disruption, and clear communication. Standard quarterly reviews and normal patching cycles are sufficient.
Contain means staying with the vendor short-term while reducing your exposure. This involves network segmentation to limit blast radius, enhanced monitoring of the appliance, stricter access controls on management interfaces, and more frequent review cycles. Contain is a transitional state: you are buying time while evaluating alternatives.
Change means planning and executing a migration to a different vendor. This is appropriate when exploitation signals are frequent, patch responsiveness is poor, operational burden is high, or the vendor's transparency and guidance quality have degraded. Set a realistic timeline (typically 90 days for planning and pilot, then phased rollout) and budget accordingly.
Vendor Scorecard
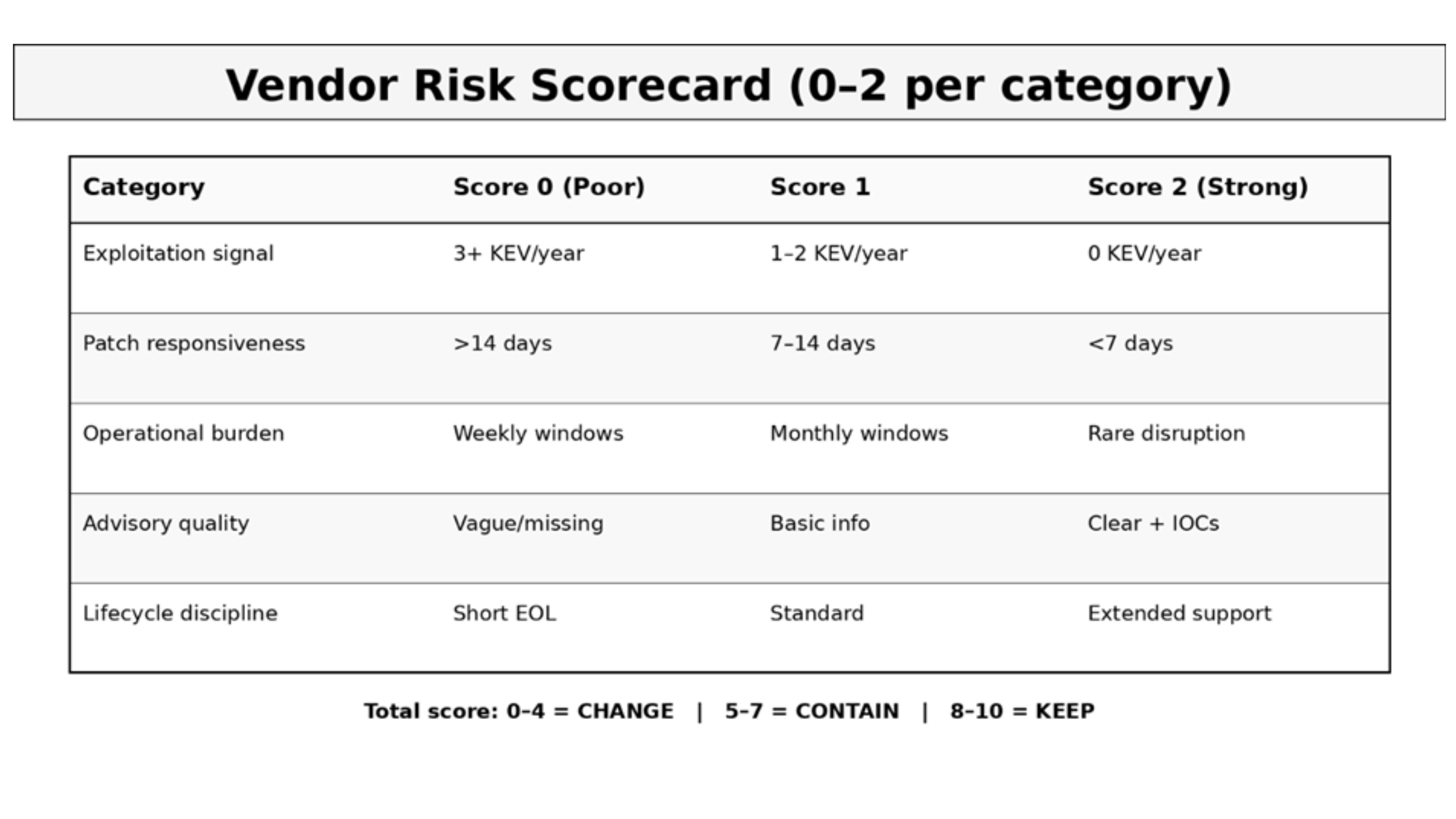
Score your vendor on five dimensions to make the decision more objective. Each category receives a score from 0 (poor) to 2 (strong).
Figure 4: Vendor risk scorecard for quarterly assessment
Decision threshold: If your vendor scores 0-1 in both exploitation signal and patch responsiveness for two consecutive quarters, initiate migration planning. Do not wait for a third bad quarter.
Making It Formal: Contract and Procurement Language
For UK organizations, the NCSC's Cyber Essentials Supply Chain Playbook provides a model for setting supplier security expectations. Turn your scorecard into contract language: require vendors to disclose KEV-listed vulnerabilities within 24 hours, provide patches within defined timeframes, and maintain transparent security advisories. Use Cyber Essentials as the minimum baseline expectation for any technology supplier in your procurement process.
Switching Without Chaos: Migration Strategy
Avoid the "rip and replace weekend" trap. Firewall migrations that attempt to swap everything at once invite disaster: configuration errors, connectivity failures, and extended downtime. A phased approach is safer and more manageable for SMB resources.
Phase 1: Reduce exposure. Before any hardware changes, lock down administrative access on existing devices. Implement management plane isolation. Remove unnecessary services from internet exposure. This reduces risk during the transition period and may buy you time if a new vulnerability emerges mid-migration.
Phase 2: Pilot in parallel. Deploy the replacement solution alongside your existing infrastructure. Start with a single site, a non-critical segment, or a specific use case. Validate configuration, performance, and monitoring integration before expanding.
Phase 3: VPN and remote access last. Remote access services affect every user working outside the office. Migrate these only after you have validated the new platform on other traffic. Ensure rollback procedures are tested, and communication plans are ready for users who may experience temporary disruption.
Owner checklist for migration: budget line items for hardware, implementation services, and a downtime buffer; MSP capacity confirmation and agreed change windows; user communication templates; and success criteria for each phase before proceeding to the next.
The Long-Term Fix: Baseline Controls
You cannot control when your vendor will disclose the next critical vulnerability. You can control how resilient your organization is when it happens. UK baseline security frameworks, particularly Cyber Essentials and the NCSC Supply Chain Playbook, provide the foundation.
Secure configuration: Disable features you do not use. If FortiCloud SSO is not required, turn it off. If management interfaces do not need internet access, remove that access. Every unnecessary service is an unnecessary attack surface.
Update management: Establish clear policies for routine updates and emergency patches. Know your maintenance windows. Know your rollback procedures. Practice them before you need them.
Access control: Administrative access to security appliances should be tightly controlled. Named accounts, strong authentication, IP restrictions, and audit logging are all essential.
Supplier expectations: Use the Supply Chain Playbook approach to make these expectations formal. Your firewall vendor is part of your supply chain, and their security practices directly affect your risk.
What to Do Next
If you use Fortinet or SonicWall, do not panic. Do two things this week: run the triage checklist from Section 5 and score your vendor using the framework in Section 6.
Ask your IT lead or MSP for your vendor scorecard results. If they cannot produce one, that itself is valuable information. Schedule quarterly vendor health reviews going forward. Make vendor risk a standing agenda item, not something you address only when the next CVE drops.
Security is not about having perfect vendors. It is about knowing your risks, having systematic responses, and making informed decisions about when good enough is no longer good enough.
Mauven’s take: Turning Vendor Risk Into A Competitive Advantage
Mauven MacLeod is a former UK cyber analyst who now provides strategic security guidance to SMBs. Here's her perspective on using this vendor risk framework to strengthen your market position and secure board buy-in.
The Competitive Advantage Play
Kathryn's given you a brilliant framework here - that vendor scorecard and 3C model are exactly the kind of systematic approach I used to look for when assessing suppliers in government procurement. Now let me show you how to weaponise it for commercial advantage.
Here's what most SMBs miss: while your competitors are pretending their firewall "just works," you're conducting quarterly vendor security scorecards using CISA KEV data and Kathryn's decision framework. That's not paranoia - that's professional risk management, and it's exactly what larger organisations do. The difference is that you can move faster and demonstrate it more clearly.
From my government background, supplier security posture was always a critical evaluation criterion. The private sector is finally catching up, especially post-pandemic. When you include Kathryn's vendor risk assessment methodology in RFP responses - the actual scorecard, the 3C decision framework, the emergency triage playbook - you're speaking the language of enterprise security governance at SMB pricing. That's a genuine differentiator that buyers understand and value.
Practical implementation:
Take Kathryn's vendor scorecard template and fill it in for your current vendor (be brutally honest)
Create a one-page summary for tender responses, showing your quarterly assessment process
Demonstrate your 48-hour KEV response capability with timestamped documentation from the last incident
Reference the specific NCSC guidance Kathryn cited - Supply Chain Playbook and Cyber Essentials
Position it as "enterprise-grade security governance adapted for SMB operations"
When prospects ask about your security, don't just say "we patch regularly." Show them your completed vendor scorecard with actual scores. Walk them through your 3C decision framework using Kathryn's model. Explain how you responded to CVE-2026-24858 or CVE-2025-40602 within 24 hours using the triage playbook. That's organisational maturity that sets you miles apart from competitors who treat security as an IT checkbox.
The April 2026 Cyber Essentials v3.3 opportunity that Kathryn mentioned: The new supply chain requirements create perfect timing. Your documented vendor risk management using this framework directly supports certification requirements while competitors scramble to retrofit compliance. Market yourself as "Cyber Essentials v3.3 Ready" and back it up with quarterly vendor scorecard data. Certification bodies love seeing systematic processes.
If you're planning a firewall migration using Kathryn's phased approach and scorecard decision threshold, that's not a weakness to hide from clients - it's leadership worth advertising. Frame it as "upgrading our perimeter security based on systematic risk assessment, not waiting for a breach to force the decision." Show them the scorecard that triggered your "Change" decision. That's the difference between reactive security and strategic risk management.
Bottom line: Kathryn's built you a complete decision framework. Now use it as a sales tool, not just an operations manual.
Selling It to Your Board: The Business Case Framework
Your board doesn't care about CVE numbers. They care about operational resilience, regulatory exposure, and whether the business can function. Here's how to translate vendor risk into their language.
Frame It as Business Continuity
Technical language: "Our firewall vendor has had four KEV-listed vulnerabilities in three months"
Board language: "Our ability to process customer transactions safely depends on a vendor with demonstrated, recurring security failures that are being actively exploited by attackers right now. Each vulnerability creates a potential business interruption window."
Insurance Implications Are Concrete Costs
Cyber insurance underwriters are asking specific questions about perimeter security and patch management in renewal questionnaires. Multiple KEV listings for your vendor will trigger red flags.
Present this as a measurable financial risk:
High-KEV-count vendors may increase premiums 15-30% at renewal
Some insurers implement coverage exclusions for perimeter breaches
Poor patch discipline can result in a refusal of renewal
Document your KEV response procedures as evidence of due diligence
From my government experience, insurance companies now employ former NCSC analysts as risk assessors. They understand KEV data, and they will ask about it.
Director Liability Under UK Law
This is the conversation that gets board attention immediately. Under UK regulations, directors have a duty of care regarding cyber risk. If your organisation suffers a breach through a known vulnerability that was KEV-listed but unpatched, that creates potential personal exposure for directors.
Key points for director liability:
The ICO has repeatedly stated that "we didn't know" is not a defence when vulnerabilities were publicly documented
CISA KEV catalogue provides documented evidence of known, actively exploited vulnerabilities
Failure to act on documented, exploited vulnerabilities can demonstrate negligence
Directors can face personal liability under gross negligence provisions
This isn't theoretical. The ICO enforcement actions increasingly reference whether organisations acted on known vulnerabilities. KEV listings establish that knowledge formally.
The Risk-Adjusted Business Case
Present costs with proper risk weighting:
Current state annual risk-adjusted cost:
Emergency patching disruption: £8,000-£12,000 (certain cost)
Productivity loss from unplanned downtime: £15,000-£25,000 (certain cost)
Insurance premium increase: £5,000-£15,000 (high probability)
Potential breach incident costs: £50,000-£200,000 (10-15% annual probability)
Total risk-adjusted annual cost: £78,000-£252,000
Migration option one-time cost:
Hardware replacement: £15,000-£40,000
Implementation services: £10,000-£20,000
Training and contingency: £7,000-£15,000
Total migration cost: £32,000-£75,000
Decision framework: Every quarter we operate on a vendor with poor KEV performance, we accept a 5-10% probability of exploitation. Over 12 months, that compounds to unacceptable levels. Migration is insurance we control, not insurance we purchase.
The Compliance Angle
From my NCSC experience, I can tell you that Cyber Essentials auditors are increasingly sophisticated about vendor risk. The Supply Chain Playbook explicitly requires organisations to assess supplier security practices. Your vendor's KEV track record will come up in certification conversations.
Position migration as a compliance investment:
Supports Cyber Essentials certification requirements
Demonstrates Supply Chain Playbook compliance
Shows due diligence for regulatory reporting
Provides an audit trail of risk-based decision-making
Bottom line for the board: Security isn't about having perfect vendors. It's about knowing your risks, having systematic responses, and making evidence-based decisions about when acceptable risk becomes unacceptable exposure. This vendor scorecard framework gives you that evidence base.
When you can show the board a quarterly scorecard with objective metrics, a documented decision framework, and risk-adjusted cost analysis, you're speaking their language. That's how you secure budget approval for migration or justify continued investment in enhanced controls.
| Source | Article |
|---|---|
| CISA | Known Exploited Vulnerabilities Catalog |
| CISA KEV Data | KEV Catalog Raw Data (CSV) |
| NIST NVD | CVE-2026-24858 Detail |
| NIST NVD | CVE-2025-59718 Detail |
| NIST NVD | CVE-2025-40602 Detail |
| NIST NVD | CVE-2024-53704 Detail |
| CVE Program | CVE Record: CVE-2026-24858 |
| NCSC | Cyber Essentials Supply Chain Playbook (PDF) |
| Fortinet PSIRT | FortiGuard PSIRT Advisories |
| SonicWall PSIRT | SonicWall PSIRT Vulnerability List |
| UK ICO | Data Security Breach Reporting |
| NCSC | Cyber Essentials Scheme Guidance |