January 2026 Patch Tuesday: New Year, New Nightmares for SMB Security
Are you feeling refreshed yet? Microsoft certainly didn’t ease us into 2026 – the January 2026 Patch Tuesday dump includes 114 fixes, with three zero‑days and one already under active attack. For battle-worn IT pros, it’s the same painful song: a heap of critical patches, exploitation in the wild, and the clock ticking before attackers turn your network into their playground.
This blog post cuts through the noise, highlights the worst flaws (by CVE), and delivers a brutally direct call to action. Short paragraphs, UK spelling, and a slightly sarcastic, highly engaging tone are all on the menu – because frankly, we’re sick of people repeating the same security mistakes.
Ready to feel the heat? Let’s dive in, and remember: patch today, not tomorrow.
The Actively Exploited DWM Zero‑Day (CVE-2026-20805)
The priority is a Windows bug that’s already actively exploited: CVE-2026-20805, an information disclosure in the Desktop Window Manager (DWM). Don’t let the CVSS 5.5 fool you – this “polite”-looking flaw is helping attackers right now. Microsoft confirmed targeted attacks using it. What’s the big deal? In simple terms, DWM can leak memory addresses, undermining defenses like ASLR and making code execution exploits much more reliable. It’s essentially giving hackers a roadmap to your system’s internals.
Are you patching this today, or are you “waiting to become evidence” as our sarcastic friend Graham quipped? Every moment of delay is an invitation for attackers to chain this leak with something nastier and walk right in. Risk-based prioritisation says treat this like a 10/10, not the “Important” label Microsoft slapped on it. Patch it now – before your network’s window (manager) gets smashed.
Old Tech, New Exploits: Ancient Modem Driver (CVE-2023-31096)
Next up is a vulnerability that made me double-check the date. CVE-2023-31096 is an elevation of privilege in a Gearsoft (Agere) modem driver – yes, a dial-up modem driver in 2026. If you’re still running an old PCI Soft Modem (AGRSM64.sys), I have to ask: what else are you running? Windows XP hiding in a cupboard? A dot-matrix printer with feelings? This bug lets an attacker with low privileges gain SYSTEM rights on your machine. That’s the master key: once they’re SYSTEM, they own you. Microsoft actually removed these dusty drivers from Windows rather than leave the risk open.
Why? Because even if you forgot about your ancient modem, hackers did not – there was public exploit code out for a similar driver for two years, and adversaries have been living off the land(line) with these “dusty old” drivers.
Think about that: an attacker doesn’t need you to have a phone line plugged in; the mere presence of the vulnerable driver on your system is enough to give them SYSTEM access. If that doesn’t make you shudder, I don’t know what will. Do you even know what outdated drivers lurk on your endpoints, or will you only find out after a breach? This isn’t trivia – it’s a likely path for ransomware gangs or state actors to burrow deeper into your network. Purge these relics and patch your systems. If you’ve got a modem in 2026, you’ve got bigger problems, but let’s start with closing this privilege-escalation hole.
Attackers Had a Head Start: XAML Diagnostics EoP (CVE-2023-37991)
Microsoft also patched CVE-2023-37991, a Windows XAML Diagnostics vulnerability that grants privilege escalation. Here’s the kicker: this bug was publicly disclosed months ago. In other words, attackers may have been tearing it apart long before you even heard of it. (Microsoft reportedly sat on the fix, which does not help you – it helps the people trying to break in.) There’s no evidence of active exploitation yet, but let’s not be naive – public exploit write-ups are basically a gift to attackers. Are you patching on the attackers’ timeline or yours? Every day of delay is a day they could be exploiting this on unpatched systems. Treat any publicly known vulnerability as urgent, even if Microsoft gives it an “Important” rating. This XAML Diagnostics bug may allow a standard user to surreptitiously gain admin privileges. Think of it like someone finding a side door to the admin office that’s been left ajar for months. It’s high time to slam it shut. Patch CVE-2023-37991 now, and if you have threat hunting capabilities, look for any suspicious elevation-of-privilege activity around XAML or debugging features. The attackers got a head start on this one – you need to play catch-up fast. Don’t patch it last because the CVSS score is middling; patch it first because the details are readily available.
🚨SharePoint ‘Toolshell’ Under Siege (CVE-2025-53770 & CVE-2025-53771)
Big red alarm here: if you run on-premises SharePoint Server, drop everything and patch now. A campaign dubbed “Toolshell” is ripping through SharePoint servers worldwide, and it’s no exaggeration to say major organisations have been hit – governments, universities, energy companies, telecoms, you name it. The primary culprit is CVE-2025-53770, a SharePoint remote code execution flaw with a severity rating of 9.8 (critical). It’s an insecure deserialization bug that lets an unauthenticated attacker from the internet run arbitrary code on your SharePoint server. In plain English: an external attacker can pull the pin and grenade your SharePoint – upload web shells, steal data, you get the picture. Supporting the carnage is CVE-2025-53771, a related vulnerability (CVSS in the 6–7 range) that enables authentication bypass and path traversal tricks. Essentially, 53771 helps the attacker move and hide – it’s a spoofing/path traversal that lets them bypass normal auth checks and navigate your server’s files at will. Together, these flaws form the “Toolshell” exploit chain, enabling a complete SharePoint Server takeover.
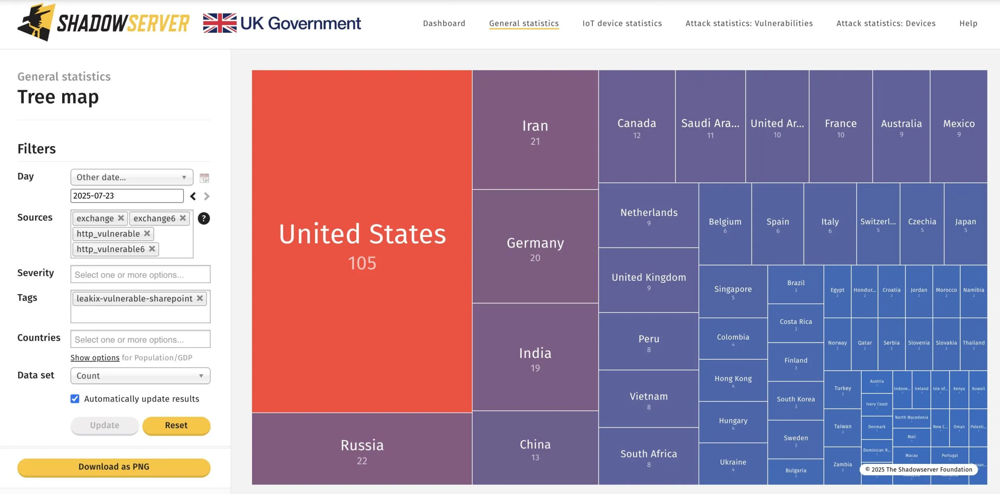
Figure: Geographic breakdown of 424 SharePoint servers still unpatched against Toolshell (CVE-2025-53770/53771) as of July 2025. The US leads, but this is a global crisis. Major incidents hit over 100 organisations across energy, finance, academia, telecoms, and even a U.S. nuclear agency
Microsoft first patched these in July 2025, but guess what – their initial fix was incomplete and attackers found a way around it within days. By December, just before Christmas, a new wave of attacks was in full swing (happy holidays, everyone!). If you haven’t patched today, assume compromise. That’s right: act as if your SharePoint is already breached and start incident response now. Look for suspicious user accounts, unexpected file modifications, or one of those lovely China Chopper or AntSword web shell signatures on your server. This is not theoretical – Toolshell attacks began months ago and are ongoing, including ransomware groups piggybacking on unpatched servers. Do you know who in your organisation “owns” the SharePoint server, and can you reach them in the next 10 minutes? If not, you have a leadership failure as much as a technical one. CVE-2025-53770 (SharePoint Toolshell) is the headline of January 2026 Patch Tuesday – it’s that urgent. Patch it yesterday, then prove your SharePoint isn’t harboring enemy code. Remember, patching stops new break-ins, but it doesn’t kick out an attacker who already planted a backdoor. That’s on you. So patch, reboot (yes, restart IIS as Microsoft advises, not just apply and pray), and hunt for signs of foul play. This is your internal website and document store – treat it like the crown jewels under assault, because it is.
.NET Kestrel Web Server Hole (CVE-2025-55315)
Do you run websites or applications on ASP.NET Core? Then pay attention: CVE-2025-55315 is a critical flaw in Kestrel, the .NET Core web server, rated CVSS 9.9. Microsoft gave this one its highest-ever severity for .NET, and for good reason – it enables HTTP request smuggling. In practice, an attacker can craft malicious HTTP requests that sneak past your server’s normal checks, essentially smuggling a second, hidden request through Kestrel. Think of it like a stranger tailgating through a secure door behind an employee – the security gate (your app) thinks everything’s fine, but an uninvited guest just waltzed in. This could let an attacker bypass authentication, ignore cross-site request forgery protections, or perform admin-only actions while the app blissfully thinks the user is legit. It’s terrifying if your application isn’t written with extreme caution. Microsoft’s security program manager for ASP.NET even said an attacker might log in as a different user or skip essential checks entirely. Do you like the idea of a stranger walking around your web app with a fake pass? Didn’t think so.
Now, patching this isn’t as simple as Windows Update. The fix requires updating your .NET runtime and possibly rebuilding your apps. Microsoft released updated .NET versions (.NET 8.0.21 and .NET 9.0.10, among others) that include the Kestrel fix. You need to deploy those, and if you have self-contained deployments, you must recompile and redeploy each app using the new libraries. This is where many SMBs falter: do you know which team (or person) can update and redeploy your web applications safely? Or are you relying on one heroic developer and a prayer? The window for exploitation is open until your web server actually runs the fixed version. Attackers are likely scanning for exposed Kestrel instances (think of all those API endpoints and IoT backends running on ASP.NET). CVE-2025-55315 (.NET Kestrel) is a nightmare because it potentially punches through multiple layers of defense. Even if you have a WAF, a cleverly smuggled request might circumvent it. This is a supply chain exposure too – if you use third-party web apps or appliances built on Kestrel, you better check with those vendors on an update. Bottom line: patch your .NET, update your apps, test them, and do it fast. If this sounds complex, well, it is. But the alternative is leaving a 9.9-rated hole in the heart of your web infrastructure – essentially an open invitation for intruders to come and go without tripping the alarm.
Critical SAP Vulnerabilities: Your Business Crown Jewels
On Patch Tuesday, SAP also dropped updates resolving a slew of critical issues. If you’re thinking “SAP doesn’t concern me,” think again – SAP runs the financials, HR, supply chain, and operations of many businesses. These are the systems that literally keep the lights on and the money flowing. In January 2026, SAP released 17 security notes, with four rated as critical “HotNews” (CVSS 9.0+). The most severe is CVE-2026-0501, a 9.9/10 SQL injection in S/4HANA Financials. An authenticated low-privilege user can execute arbitrary SQL queries – meaning they can read or modify financial records at will. In essence, your junior accountant could become a database superuser by accident (or a malicious insider could). Another is CVE-2026-0500, a 9.6 RCE in SAP Wily Introscope (an application monitoring tool) that allows unauthenticated complete system takeover. There’s also an 8.8 privilege escalation in SAP HANA (CVE-2026-0492) that can compromise your database integrity, and likely an arbitrary file write or path traversal in the mix as well. In summary: code execution, SQL injection, auth bypass, file write – all the greatest hits, in the very core systems that handle your company’s secrets.
If you have SAP, patch it like it matters. Too often, organisations treat SAP and other ERP updates as “we’ll schedule it next quarter” because they’re scared of downtime. Meanwhile, attackers salivate at the chance to quietly inject themselves into your ERP and siphon off data (or worse, alter records). Do you patch your SAP applications with the same urgency as Windows? You should. A critical SAP breach can be existential for a business – think of an attacker with full access to your financial system or supply chain management, possibly undetected for weeks. Also, patching SAP might require coordination with your SAP administrators or even consultants – get them on the phone now. Plan the updates and apply them pronto, ideally in your next maintenance window (if not sooner for the really critical ones). Remember, unauthorised access to core business systems can mean fraud, IP theft, or total disruption. The bad guys know enterprises are slow to patch SAP, which makes these bugs low-hanging fruit. Surprise them by being on top of it.
And one more thing – if you rely on a service provider or MSP to manage your SAP, hold their feet to the fire about these patches. Supply chain risk isn’t just about code libraries; it’s also about the admins managing your crown jewels. Insist they apply SAP’s January fixes immediately. In cybersecurity, shrugging off an SAP patch is like leaving the vault door ajar. Don’t do it.
Apple’s WebKit Zero‑Days: Patch Your iPhones, iPads, Macs
Quick sweep beyond Microsoft: Apple had its own scare recently. On December 12, 2025, Apple pushed out emergency patches for two WebKit zero-day vulnerabilities being used in targeted attacks. WebKit is the browser engine under Safari (and all browsers on iOS), so these flaws affect iPhones, iPads, and Macs. One was linked to mercenary spyware, meaning professional hackers were actively exploiting it against high-value targets. These vulnerabilities allowed attackers to execute arbitrary code via malicious web content – just visiting a rigged website (or viewing a booby-trapped web ad or PDF) could silently compromise the device. Apple confirmed attackers were already exploiting them in the wild. If that doesn’t scream urgency, I don’t know what does.
So, what’s the status now? Apple released iOS/iPadOS 26.2 and macOS updates that fix these Apple WebKit zero-days. The catch? Many users haven’t updated! As of early January 2026, adoption of iOS 26.2 was shockingly low (one report said only ~4.6% of iPhones were on 26.2). That means a vast majority of devices are still vulnerable. If you manage Apple devices in your business, make sure those updates are installed now. Do you enforce mobile device updates via MDM, or do you let employees click “Remind me later” indefinitely? It’s a serious question. Corporate iPhones often sit on outdated versions because users delay and IT doesn’t follow up. Hope is not a strategy here. These WebKit flaws can lead to spyware on executives’ phones – reading emails, listening via microphone, stealing credentials, you name it.
And don’t forget Macs – plenty of SMBs have a few MacBooks around (design team, CEO’s fancy laptop, etc.). Those need patching too, as Safari/WebKit issues impact macOS. Apple’s updates also introduced a new security feature (Memory Integrity Enforcement) that older iOS versions lack. Only devices on the latest release get the full protection. Make it policy to force-restart and update Apple devices. Yes, people hate restarts, but guess what: restarting also flushes any spyware that’s only in memory. Many high-end iPhone exploits don’t survive a reboot (they rely on not being persistent to avoid detection). By pushing that iOS 26.2 update, you not only patch the holes but also boot out any in-memory malware that might already be lurking. It’s a win-win – if you actually do it. So, do it. Apple WebKit zero-days may sound like something only affecting journalists or diplomats, but today’s targeted attack becomes tomorrow’s commodity exploit. Don’t wait until everyone is a target. Patch your Apple gear and ensure those “Later” buttons get pressed now, not on St. Never’s Day.
Adobe Acrobat & Creative Cloud: Professional Files, Hidden Threats
Now onto Adobe. January’s Adobe updates might not grab headlines like a zero-day, but ignoring them would be a mistake. Adobe delivered patches for dozens of vulnerabilities across Acrobat, Reader, Photoshop, After Effects, Animate, and more. In total, over 30 flaws were fixed, with at least 8 critical ones that allow arbitrary code execution. Translation: opening a PDF or an Adobe project file could let an attacker run malware on your system if you’re unpatched. How many PDFs pass through your business each week? Hundreds? Thousands? Adobe Acrobat vulnerabilities matter because we all treat PDFs as benign – invoices, contracts, reports – yet they’re a top target for exploitation. The January fixes include critical RCE bugs in Acrobat and Reader (Windows and macOS). Adobe themselves warned that malicious actors could exploit these to hijack systems via specially crafted files. There’s no evidence (yet) of these particular bugs being exploited in the wild, and we’d like to keep it that way!
Also patched were Adobe Photoshop, Illustrator (iPad), Animate, and multiple 3D apps. Think about your marketing or design department – they regularly receive and open files from external sources (images, graphics, project files). If those files are booby-trapped, an unpatched Photoshop or After Effects could be the entry point for a breach. It sounds sensational, but it’s absolutely possible. Booby-trapped creative files are a real tactic (imagine a malicious .psd file delivering payloads). Adobe said some of these critical flaws could lead to code execution just by opening a file, and none require any weird user interaction beyond that. That’s as easy as tricking someone into viewing a fancy graphic or animation.
So, what to do? Patch Adobe products via the Creative Cloud updater or your software management tool. Adobe’s patches are out – use them. In particular, get everyone on the latest Acrobat/Reader; those are common across all departments (finance, HR, etc.). Remember, PDF attachments arrive daily and often slip past email filters if they’re not known malware. Users double-click PDFs without a second thought. We must ensure that action can’t silently compromise their PC. And a pro tip: consider enabling Protected Mode/Protected View in Acrobat if not already – it sandboxes files from untrusted sources. But still, a sandbox isn’t foolproof if you’re unpatched. Do you treat PDFs and creative files as harmless just because they look professional? You shouldn’t. Every “trusted” file format can hide a threat. By patching Adobe Acrobat vulnerabilities and those creative app bugs, you’re closing off a whole class of drive-by attacks on your users. It’s low effort compared to dealing with a foothold because someone opened “Invoicé_Q4.pdf” that turned out to be laced with poison. So update your Adobe software, and maybe remind your team that not all PDFs are as innocent as they appear.
The Fortinet Fiasco: CVE-2020-12812 – 5 Years Unpatched?!
Time to call out some truly poor patching behavior. Fortinet – a popular firewall and VPN vendor in many SMB environments – had a critical flaw back in 2020: CVE-2020-12812. It’s a CVSS 9.8 bug in FortiOS (the firewall OS) that allows a 2FA bypass on SSL VPN. Essentially, by tweaking the case of the username during login when LDAP is used, an attacker can skip the second factor and just waltz into the VPN. Fortinet patched this in July 2020. And yet here we are, five and a half years later, and over 10,000 Fortinet firewalls are still vulnerable online. Yes, you read that right: 10,000+ firewalls exposed with a known, actively exploited hole from 2020. If you’re among those, let me put this politely: you didn’t miss a patch; you adopted a hobby. Maintaining a vulnerable device for half a decade is beyond negligence – it’s like leaving your front door not just unlocked, but hanging off the hinges, and then going on holiday.
This flaw isn’t theoretical anymore. As of December 2025, Fortinet themselves warned that attackers are actively abusing this old CVE in the wild. Multiple ransomware groups (like Play and Hive) and even state-sponsored APT actors have leveraged it to breach organisations. It was added to CISA’s Known Exploited Vulnerabilities catalog way back in 2021, with a U.S. federal agencies deadline to fix by May 2022. So there’s really no excuse. If you still have CVE-2020-12812 unpatched on a FortiGate, you’re basically begging to be hacked. Do you prefer planned downtime or the surprise version with ransom notes? Because those are the options. Shadowserver Foundation scanning shows ~9,700 vulnerable instances globally as of the end of 2025, including over 1,200 in the US alone. The enemy can count how many juicy targets remain, and you better believe they’re picking them off.
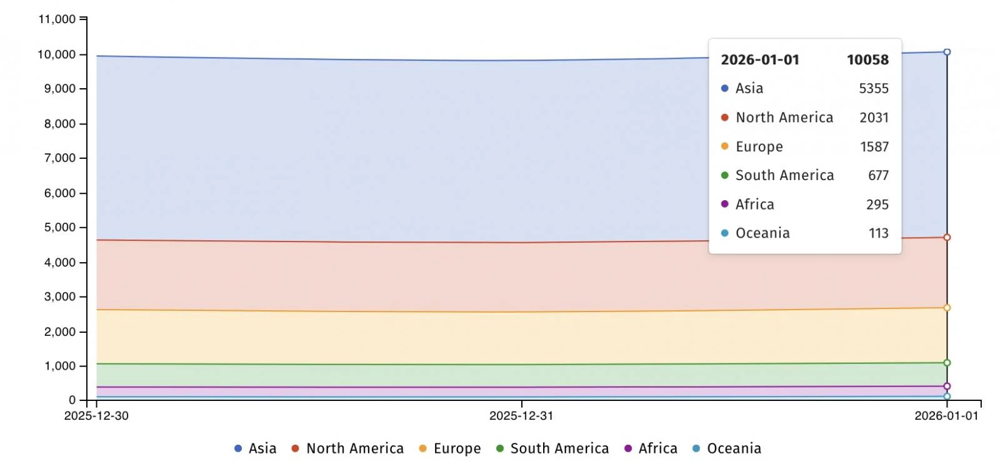
Figure: Count of internet-exposed Fortinet firewalls still unpatched for CVE-2020-12812 as of Jan 2026 (total ~10,000). Each region’s share is shown (Asia-Pacific in red has ~53%, North America ~20%, Europe ~16%, etc.). This 5-year-old 2FA bypass is actively exploited by ransomware gangs and APTs – patch or perish.
Making matters worse, new Fortinet vulnerabilities popped up in December 2025. Specifically, CVE-2025-59718 and CVE-2025-59719 – both FortiOS/FortiProxy authentication bypasses related to FortiCloud SSO, rated around 9.1–9.8 critical. These allow an attacker to log in as an admin without credentials by forging a malicious SAML login (if you had FortiCloud SSO enabled). And guess what? Within 3 days of disclosure, attackers were actively exploiting 59718/59719 in the wild (Arctic Wolf observed intrusions on Dec 12, 2025, less than a week after the patch). That’s Formula 1 speed in the hacking world. Fortinet rushed out patches on Dec 9, and CISA added CVE-2025-59718 to the KEV catalog by Dec 16, with a directive for agencies to patch by December 23, 2025. (In other words, if you hadn’t patched within two weeks, you were already late.)
Let me translate this into plain speak: If a government cybersecurity agency sets a two-week deadline on a vuln, why on Earth would you set a later one for yourself? These Fortinet issues – both the ancient CVE-2020-12812 and the new CVE-2025-59718/59719 – highlight a chronic problem: edge devices often get overlooked in patch cycles. They’re “set and forget” until they become the hole that lets attackers in. Don’t forget them. Check your Fortinet firmware versions now. If you’re behind, get those updates scheduled immediately, even if it means some downtime. The alternative might be far worse downtime when ransomware locks up your network. And for the love of all that’s holy, if you can’t patch (maybe you’re on an old end-of-life model?), at least implement mitigations: e.g., disable FortiCloud SSO login feature if you’re not using it (it’s off by default unless you enabled it during registration), restrict admin access to known IPs, etc.. But ultimately, patching is the fix. Fortinet appliances sit at your network perimeter – if they fall, everything behind them is up for grabs. So patch your firewalls, or they will become the fire, walloping you.
HPE OneView RCE (CVE-2025-37164): An Unauthenticated 10.0
Moving on to another often-forgotten piece of infrastructure: HPE OneView. This is HPE’s data centre management appliance – essentially controlling servers, storage, networking in an HPE environment. Even if you’re a small business, you might have a ProLiant or two with OneView running the show. Well, in December 2025, HPE disclosed CVE-2025-37164, a CVSS 10.0 (perfect score) unauthenticated RCE in OneView. This means anyone who can reach your OneView interface can execute code on it, without logging in. The issue lies in an unsecured REST API endpoint – basically, OneView wasn’t validating requests properly, allowing remote code injection. If OneView is compromised, an attacker potentially has control over all the infrastructure it manages (think: altering your server configurations, messing with storage volumes, injecting firmware malware, etc.). It’s hard to overstate how bad that could be – it’s like hijacking the control tower of an airport.
HPE did release a patch/hotfix (all OneView versions up to 10.20 are affected, and presumably fixed in a version 11 or hotfix). But here’s the scary bit: within ONE day of HPE’s patch, a Metasploit module was released by Rapid7 to exploit this vulnerability. Public proof-of-concept code is out – script kiddies and low-tier attackers can now just point-and-click own any unpatched OneView instance. CISA added this to the KEV catalog as well, giving U.S. agencies until Jan 28, 2026 to remediate. So the clock is ticking. If you run HPE OneView, find out where it’s running and patch it immediately. Don’t assume “oh, it’s an internal appliance, we’re safe behind our firewall”. OneView often runs on a separate management network, but if an attacker ever lands on an internal network (phishing, malware on a PC, etc.), guess what they’ll target next? Your unpatched OneView, because it’s a gateway to everything. We’ve seen it time and again: attackers love to hit VMware vCenter, storage controllers, and management appliances – because owning those gives them persistence and broad access.
And note: patching might be non-trivial. OneView could be a virtual appliance or physical. Schedule the update and follow HPE’s instructions. If for some reason you cannot patch in the next day or two, at least restrict network access to OneView’s interface (VPN only, IP whitelist, etc.). But really, no excuses here – CVSS 10 means a straightforward remote exploit that will be used in the wild (if it isn’t already). As one expert said, public exploits exist now – it’s not a theoretical risk. And since OneView manages things like firmware, an attacker could even create destructive effects (imagine them bricking your iLO interfaces or wiping config – that’s an IT nightmare). So treat this as urgent. Do you even know where your OneView lives and who can patch it today? If not, figure it out – and if you don’t have OneView, double-check you’re not using some OEM rebranded version (e.g., some Cisco or Dell gear in the past bundled HPE OneView for blade systems). The takeaway: CVE-2025-37164 (HPE OneView) – patch it or disconnect it, but do not leave it exposed.
VMware ESXi: Patch Backlogs & “Assume Breach”
Finally, a word on VMware ESXi, the virtualisation platform that many SMBs and virtually all enterprises rely on. ESXi had a rough time last year – in March 2025, VMware (Broadcom) patched three ESXi zero-days that were already being exploited. Those flaws (CVE-2025-22224, 22225, 22226) allowed attackers to break out of a guest VM and execute code on the hypervisor itself, essentially compromising the entire host and all its VMs. It was big news, and patches came out, but not everyone updated promptly. Fast forward to December 2025: a Chinese hacking group used an exploit chain that very likely included those March 2025 ESXi vulnerabilities to compromise an organisation’s ESXi hosts nearly a year after the fixes were available. In other words, old ESXi bugs were still yielding paydirt for attackers. They even developed a sophisticated toolkit (named “MAESTRO” by researchers) that chains these bugs to escape VMs and plant backdoors on the hypervisor. The kicker: clues suggest the exploit was ready and tested by the attackers in early 2024, long before VMware disclosed the flaws publicly. This implies some threat actors might have had zero-day access and then continued using it even post-patch against un-updated targets.
What’s the lesson here? Patching isn’t just about the latest updates, it’s about catching up on last year’s updates too. Many organisations apply new patches but never go back to fix older ones, especially if they missed the memo. Attackers don’t forget – they probe for any known hole, old or new. And with hypervisors like ESXi, a single compromise can mean all your virtual servers are at risk simultaneously. We’re talking domain controllers, file servers, application servers – if ESXi is popped, it’s game over (ransomware actors demonstrated this with ESXiArgs ransomware attacks in the past). So, if you haven’t patched ESXi in a while, you’re a sitting duck. Get on whatever the latest ESXi update is for your version (and note: some patches might involve updating vCenter too, and possibly firmware if those bugs were deep).
Importantly, verification is key. Did you patch ESXi and also check for signs of compromise afterward? Don’t just assume that applying the patch means all clear. If you were late and attackers had already been in, they could have left backdoors (rogue VMs, altered ESXi host images, malicious cron jobs on the host, etc.). VMware provides guidelines for checking integrity – use them. Look at your host logs, check for unusual accounts or VMs you don’t recognise. As Graham Faulkner said, “patching is not just about the latest updates, it is also about cleaning up the backlog and verifying compromise.” If you discover something off (like that VSOCKpuppet backdoor mentioned in some reports), you might need to do a full incident response. It’s not paranoia; it’s happened to others.
So in summary for ESXi: patch, patch, patch, then audit. If you’re on a version that’s end-of-support, plan an upgrade – unsupported hypervisors don’t get patches, and there’s no magic shield protecting them. Virtual infrastructure is “critical infrastructure” for your business. You should treat ESXi issues as top-tier priority, not “we’ll do it eventually”. And if you feel overwhelmed, get help – many SMB-focused security firms can assess your ESXi host integrity. Because the question isn’t just “Did we patch?” – it’s “Are we already owned from before we patched?” Hard question to ask, but far better to find out now than when ransomware starts shutting down all your VMs at once. Trust me, that happens, and it’s devastating.
Patching Priorities: Today, Not Tomorrow
Feeling the urgency? You should be. Let’s wrap up with a practical patching game plan, because not everything can be fixed in an hour. Here are battle-tested priorities for this Patch Tuesday haul, channeling the “do it now” attitude we need:
Within 24 hours (Immediate Emergency): Apply Windows OS updates (especially for that exploited DWM CVE-2026-20805!). Patch on-premises SharePoint yesterday – assume Toolshell CVE-2025-53770/53771 has already hit you and act accordingly. Update any Fortinet devices at the edge – both the 2020 and 2025 bugs; attackers are already in motion here. Patch HPE OneView or isolate it until you do. And push out those Apple iOS/macOS updates for the WebKit zero‑days – don’t rely on user diligence, force it via MDM if you can. These are the “drop everything” items because attackers are actively using these or ready to pounce, right now. If your team can’t get to all of them in a day, ask why? Is it change control bureaucracy? Staffing? Or wishful thinking that “eh, we’re probably not a target”? Fix that mindset before it fixes you a spot on the data breach news.
Within 72 hours (Very Urgent): Address .NET / ASP.NET (Kestrel) updates and redeploy your web apps with the patched runtime. This might take a bit more coordination (dev teams, testing), but it’s critical to do within a couple of days – a 9.9 smuggling flaw is a ticking time bomb. Next, any SAP critical patches should be applied within the week at most – ideally your BASIS team can do the four HotNews notes in a few days. Also in this bucket: Microsoft Office and Exchange fixes (there were some Outlook/Office RCEs and preview-pane issues this month – those should be fixed within a few days as they’re often phishable vectors). VMware ESXi – if not patched already – do it within 72 hours and simultaneously check for compromise as discussed. It’s a lot, yes. But better a controlled patching sprint than an uncontrolled incident.
By end of week (Routine but Important): After the crises above, mop up the rest in your normal weekly maintenance: e.g. browser updates (Chrome, Edge, Firefox had some high-severity fixes – get those auto-updates flowing), Cisco or other network gear patches (if any critical ones came out), and remaining Adobe and other third-party app updates. These may not be under active attack (yet), but leaving them unpatched indefinitely is asking for trouble. Keep your routine patching truly routine, so that next Patch Tuesday you’re not still doing last Patch Tuesday’s work.
And a special note: Legacy systems. Windows 10 (non-ESU) fell out of support in Oct 2025. That means no security patches at all for Win10 now – not even critical ones. If you still run Windows 10 anywhere important, you’re using an OS stuck in time while new vulns (and exploits) keep emerging. Not a good combo. Plan to replace or upgrade those to Windows 11 immediately. It’s like leaving a cracked window un-repairable – eventually someone will slip in. The same goes for any out-of-support software/appliances: they will become attacker favorites since everyone knows no patch is coming. Either pay for extended support (if available) or migrate off them, period.
In closing, this January 2026 Patch Tuesday is a brutal reminder that security is a race – a race between your team and the attackers. Do you want to be secure, or just hopeful? Hope doesn’t stop ransomware. Patches do. The vulnerabilities we discussed are particularly severe – many being actively exploited or trivially exploitable. If you patch today, you cut off those attack paths. If you push it to “next week” or “next month,” you’re living on borrowed time. The battle-worn veterans know the score: patch today, not tomorrow. If you’re overwhelmed, prioritise and tackle the truly critical ones first (we’ve told you which those are). Pull in outside help if needed. But don’t just shrug and defer. As our no-nonsense narrator put it, “You install the whole update or you stay exposed.” There’s no middle ground.
No fluff, no excuses – get those patches applied. The January 2026 Patch Tuesday may have started with a bang, but whether it ends badly or not is up to you. The heat is on, and the clock is ticking. Patch now and save yourself the post-breach “I wish we had…” speech. Stay safe out there – and remember, in cybersecurity, “later” is often too late.
Sources: Verified details have been drawn from Microsoft, vendor advisories, and reputable security researchers. Key references include the Zero Day Initiative review, CISA’s Known Exploited Vulnerabilities catalog updates, and first-hand analyses from security firms (e.g. Shadowserver stats on Fortinet, Huntress on ESXi exploits, Malwarebytes on Apple’s spyware-linked zero-days, among others).
The urgency and real-world exploitation described are grounded in these reports. When in doubt, consult the official advisories linked above and patch documentation for your products. Let’s make 2026 the year we finally break the cycle of delayed patching – or at least, the year we catch attackers flat-footed for once. Happy New Year – now go patch!
Sources
| Source | Article Name |
|---|---|
| Microsoft | January 2026 Security Updates Release Note |
| Zero Day Initiative | The January 2026 Security Update Review |
| CISA | Known Exploited Vulnerabilities Catalog |
| Rapid7 | CVE-2025-37164: HPE OneView Remote Code Execution |
| Shadowserver Foundation | Vulnerable Device Statistics (Fortinet, etc.) |
| Apple | About the security content of iOS 26.2 and iPadOS 26.2 |
| Adobe | Adobe Product Security Bulletins |
| Huntress | ESXi Zero Days Exploited in the Wild |
| Broadcom/VMware | VMware Security Advisories |
| SAP | SAP Security Notes - January 2026 |